The Department of Homeland Security and the Office of the Director of National Intelligence, have released their JAR, also known as a Joint Analysis Report. They called it the GRIZZLY STEPPE JAR. You can read the full publication at https://www.us-cert.gov/security-publications/GRIZZLY-STEPPE-Russian-Malicious-Cyber-Activity or you can download it from our site. JAR_16-20296A_GRIZZLY STEPPE-2016-1229
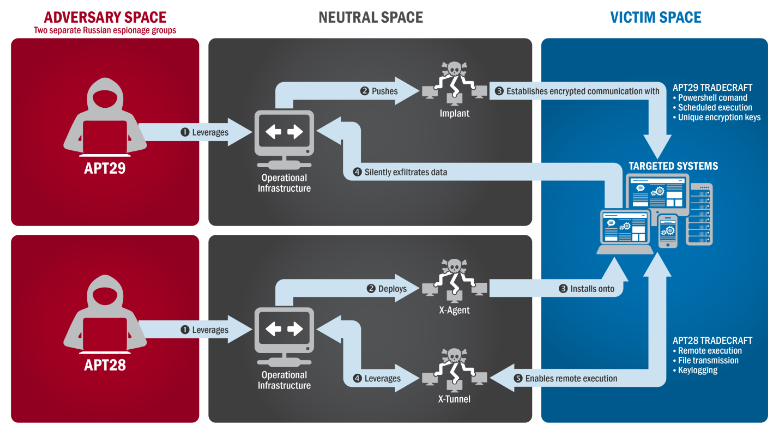
“The US Government confirms that two different RIS actors participated in the intrusion into a US political party. The first actor group, known as Advanced Persistent Threat (APT) 29, entered into the party’s systems in summer 2015, while the second, known as APT28, entered in spring 2016.” from the Joint Analysis Report GRIZZLY STEPPE
RIS actors stands for “Russian Intelligence Services”.
It was observed that APT29 used targeted spearphising campaigns in which they lure users to click on web links. Once a user would click on this link, it would install a Remote Access Tool and avoid detection. APT28 crafted domains and websites that looked like legitimate websites/applications that were used by the targeted organisation. APT28 for example made heavy use of shortened url’s to hide these domains. Once a user landed on these ‘legitimate looking’ website, they would insert their login credentials, which would then be stored by the RIS’s to collect information.
“These actors set up working infrastructure to obfuscate their source infrastructure, host domains and malware for targeting organisations, set up command and control nodes, and harvest credentials and other valuable information from their targets.” from the Joint Analysis Report GRIZZLY STEPPE
The report also describes a range of ip addresses where the attacks were orchestrated from. Urging the administrators to check their infrastructure. JAR-16-20296A
Below is a list of the resolved ip addresses, which shows where the attacks originated from.
Security specialists at WordFence went deeper into the issue, and investigated the malware that was used to take control of the systems. As it turns out, systems that made use of PHP were injected with PHP malware that allowed them to remotely management an infected system. The malware gave the actors the possibility to browse the local user filesystem, reach and possibly databases, search for files, network tools to scan for ports, bruteforce tools for passwords and a command line to run system commands.
As it turns out the Malware is publicly available and can be used by anyone who knows how to inject it into a website. Since many websites today are dynamic (thanks to ASP or PHP) this is a very valuable tool to launch an attack. Almost every forum software or content management system on the internet makes use of PHP and is a possible victim for the malware.
Author Reponse
While the malware might be ‘made in the Ukraine’, I tend to agree with WordFence on the fact it is quite odd that the Russian Intelligence Service would use a publicly available toolkit to take over websites (they should have means to develop such toolkits themselves?). The report also shows barely any real tangible evidence that points in the direction of Russia. They believe it is Russia because the ‘attack pattern looked the same like previous attacks which were Russian’. It is technically as good as impossible to determine the origin of the attack. Claiming that the malware is Russian because ‘it is written in Russian’ is a fallacy, there are non-Russians who can write Russian, or someone who wanted it to look Russian. Having the attack come from Russian servers (only a small percentage actually came from Russia) does not make the attack Russian.
Also concerning the attacks on PHP websites, it is interesting to note that the majority of attacks were done from tor-exit nodes. Tor is a network which tries to make communication more anonymous. The very same tor network of which much has been written about, and how it is not a 100% anonymity solution. Traffic going over the Tor network can still be intercepted and used against you. Not to mention the amount of overhead that having so many tor hops would have to efficiently brute force a website, it makes no sense. Rather it is more interesting to have malware installed on servers around the globe and then directly attack a target instead of going through Tor. Tor can be used to hide your identity but it is also known to be used by criminals (and the US Intelligence Services trying to get hold on as many exit nodes possible, because having many means your chances of intercepting stuff increases). Also I’m personally very sceptic against such secret agencies (remember the certainty they had about the evidence of nuclear weapons in Iraq?).
Our website also saw a very noticeable and persistent attack pattern emerging during the last month which may or not be related to this, websites get scanned and attacked every single day depending on popularity and defence measures. Having a website probed by some network/botnet by guessing login pages is (sadly) fairly common, but it was quite strange when suddenly non-default pages used as login authentication were being brute-forced by valid usernames (also non default).




Leave a Reply
You must be logged in to post a comment.