Category: Security
-
Check if your system is vulnerable for Intel’s latest security flaws
The RIDL and Fallout speculative execution attacks allow attackers to leak private data across arbitrary security boundaries on a victim system, for instance compromising data held in the cloud or leaking your data to malicious websites. Our attacks leak data by exploiting the 4 newly disclosed Microarchitectural Data Sampling (or MDS) side-channel vulnerabilities in Intel…
-
Chrome and Firefox Phishing Attack Uses Domains Identical to Known Safe Sites
Update on April 19th at noon Pacific time: Chrome has just released version 58.0.3029.81. We have confirmed that this resolves the issue and that our ‘epic.com’ test domain no longer shows as ‘epic.com’ and displays the raw punycode instead, which is ‘www.xn--e1awd7f.com’, making it clear that the domain is not ‘epic.com’. We encourage all Chrome users to…
-
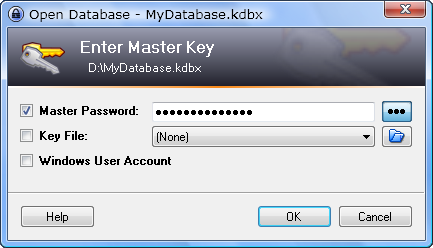
Review: Keepass
Keepass is a Password Manager, which helps you to remember your password and make secure passwords for you. Securing your online accounts is becoming more and more important, and using unique passwords for each account is very important to avoid that your other accounts get hacked when a single website or service leaked your information. This way…
You must be logged in to post a comment.